Hope you understand that a user will get a tokens pair after validating with OpenID Connect. Do you know why there are two different tokens which seemingly do the same kind of thing?
The format of token and content is not definite by the standard of Open ID connect. They may be anything. It is normal for both tokens to be comparable, most of the time set to accurately the same value, but it does not need to be.
Think carefully about OpenID Connect as a framework of authentication, except just a protocol. It can fully support any type of authentication system, with whatsoever (existing) format of a token.
There are different solutions and providers: Facebook, Gmail, Forgerock, PingFederate, Microsoft Active Directory, and more… each and every one with its own peculiarities.
As a professional developer that has to put together one of these, you would need to know what is directly or indirectly coming out of that specific provider, just that one.
Response of the Authentication
The specific application receives a reaction like this upon a thriving authentication.
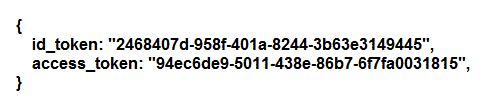
It can be a special type of format, like this as an alternative.
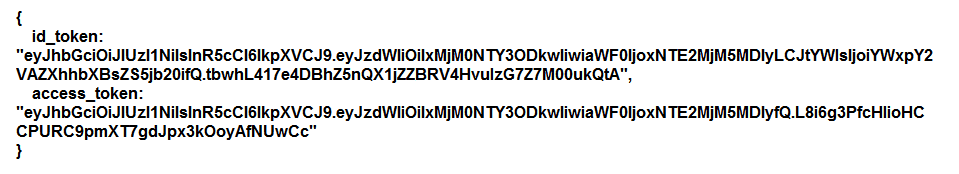
The specific session token is to be effectively saved as a human cookie in a web browser or directly passed as a header for the access like programmatic.
The thing is which particular one is the session, in case, not both? We are just about to getting into that. (You can use the access_token by rule, not just the id_token)
As a professional and experienced developer, there are two different things to perfectly care about authentication of user:
- Confirming the token is active/valid
- Getting the connected user
Black box tokens
Now we are going to discuss blackbox tokens. You don’t recognize what it actually contains.
The providers have to give APIs to confirm the token and to get back the identity of user. Carefully lookup important documentation from the specific provider.
You should know that OpenID Connect has a voluntary “/userinfo” endpoint to get back information of user. It is a wonderful starting point for a perfect research. It can take a limit to choose which specific user attributes to get (range).
The API can also accept either token, or both, see and try. Keep in mind to read the important documentation too!
You must confirm the token as well as retrieve the connected user. You are all set when you check out what API to utilize and how.

A token named JWT is an object of javascript containing information of the user, base64 encoded.
Cryptographically the token is signed and it can be confirmed utilizing the public key from the confirmation provider. There are different libraries of JWT that is available to manage this.

After perfect decoding:
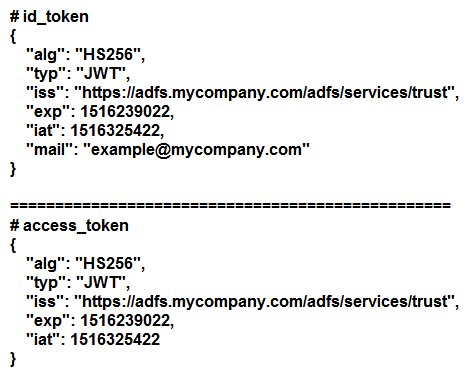
You have to suppose that the particular provider does NOT have some type of API to validate the token or to recover the identity of user. It is really not required along with JWT tokens, the whole thing required can be embedded in the particular token.
As a professional developer, you want the effective user identifier. Generally an email, a primary key, or an employee ID.
The two different tokens are mainly equivalent, apart from the mail field. Let us suppose that users are referenced by email. Understand that access_token is here valueless. It is omitted the email. It does not point out what or whom to grant complete access to?
Know that OpenID Connect does not define any needed attributes of the user. It completely depends on the provider to choose what to set. Check the documentation of provider on user claims.
You must have the chance to choose claims, first when on your OpenID Connect client boarding along with the provider of OpenID Connect, then later by utilizing a parameter of “scope” in APIs authentication.
It completely depends on the provider to honor and accept these settings of configuration. It depends on the provider that claims are supportable and supported.
Preferably, you must configure all type of tokens to carry sufficient user attributes.
You are all done when you check out which specific claim(s) you want and how you can efficiently get them.
- JWT can fairly get HTTP and large headers (together with cookies) are bound to some kilobytes. Know that limit claims to the least amount.
- It will be really very good in case the provider can have a suitable user identifier by default built-in.
Creation of Automatic Account
There is an extraordinary use case which can be well managed by OpenID Connect. Automatically making accounts for new users.
Lets think about a practical example. A user is approving to Stack Overflow utilizing Google (or Microsoft ADFS, StackOverflow Enterprise). (You cannot ask Stack Overflow for assistance earlier than getting an account of Stack Overflow).
It is a separate product with its own session management and user base. It must accept users from Facebook, Google or on premise, yet it should not completely depend on them.
It is simply noticed in practice. Originally the id_token was created for this accurate purpose.
User can start the process of authentication with the third-party service provider and come again back with the claims/tokens explained before, then:
- In case the external account completely matches an available id or email, the user is also logged in as that account (stack overflow).
- In case the external account does not match any internal account, a fresh new account is automatically created. Information of the user can be automatically filled.
The /userinfo and id_token endpoint can hold different user attributes, either when explicitly configured or by default for it. What is efficiently supported is up to the service provider.
A few providers supply the complete user profile by default to effectively cover this use case.

Conclusion
This effectively covered the most usually usages of access_token and id_token in the wild. Your mileage can differ as per on the OpenID Connect providers you must incorporate with. Famous internet service providers must be quite well standardized and documented.
- Top 6 SEO Tools to Boost Your Business - January 18, 2024
- Top PHP interview questions and answers 2020 - July 7, 2020
- How to create a Whatsapp account using the Australian number? - June 28, 2020
